Phishing Attacks: Part 2
What is Phishing?
Phishing attacks use e-mail to trick users into downloading malware onto their systems for the purpose of stealing information or placing the user in a compromising position that the attacker can exploit.
Malware can be ransomware, which encrypts all files until the victim pays a ransom – usually in bitcoin or other untraceable monetary medium. It can also be a keylogger, which sends all keystrokes back to the attacker. This includes usernames and passwords to bank accounts, credit cards, and other financial or health portals. Malware can also remotely turn on your cameras and microphones to secretly record a user, hoping to record a conversation or video that they wish to keep private.
Are You Being Phished?
Phishing attacks have become increasingly sophisticated; however, some are easy to spot, like the example below. Now I, along with several billions users, have had my Yahoo account compromised. Thus, the fact that someone has my user name is not a surprise.
Take a look at the email below.

How to Detect a Phishing Attack
Unlike the last time when I received an Apple alert, I actually do have a PayPal account. However, there are many signs that this is in fact a phishing attack.
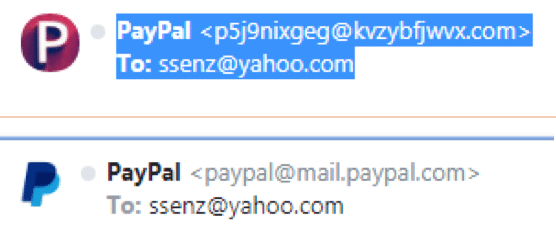
First, notice the e-mail salutation is simply ssenz@yahoo.com. This is very suspicious, as PayPal has my actual name and other personal information on file. Let’s compare that message to a legitimate one from PayPal. In the one below, the message contains my first and last name.

Now let’s compare other telltale marks between the two e-mails.
The spam e-mail has some bogus account from which the e-mail was sent and the icon associated with PayPal is all wrong.
The e-mail from the real PayPal organization shows “PayPal” and displays the correct icon for the company.
Finally let’s look at the link that both e-mails want you click.
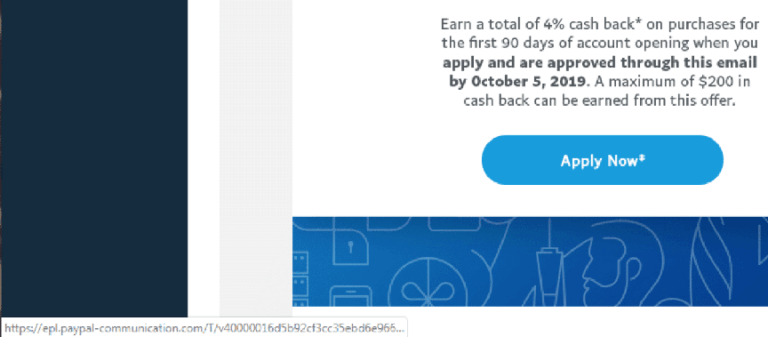
If you look closely at the link at the bottom you will see it says
Https://epl.paypal.communication.com/…
Now look at the link of the spam e-mail.
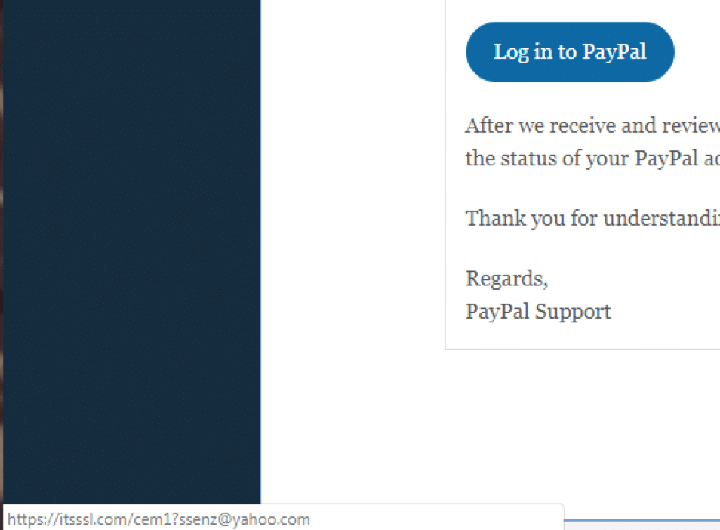
This says http://itssl.com/cem1?ssenz@yahoo.com.
Notice there is no PayPal URL in the link – so wherever you are being directed to, it is definitely not PayPal. This is what is known as a URL shortener, which allows hackers to find your other sensitive files and infect them with malware.
Finally, look at what appears at the bottom of a legitimate PayPal e-mail:
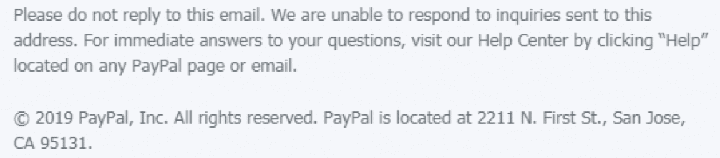
There is NO such language in the bogus PayPal e-mail.
Fortunately, this e-mail message had very obvious signs of illegitimacy. Other messages are more sophisticated and require a bit more research. I will post examples of these messages in future blogs. In the meantime – if you get any message asking you to click a link – go to the portal from which you established your account and check to see if there is anything amiss.
Tips and Tricks to Avoid Phishing Scams
This is not a very sophisticated phishing attack. There are some attacks that fool even seasoned cyber security professionals. Fortunately, there are several rules to follow that everyone should take to protect themselves.
- Never click on a link in a suspicious e-mail.
- If you are informed that an account of yours has been compromised, call the number on the back of the charge card, or log into your account. Never call the number provided in the e-mail. These are phony numbers answered by the scammers that sent out the e-mail.
- After you confirmed the e-mail was bogus, delete the e-mail, and then delete the e-mail from the trash folder.
- If you receive a message from a trusted source (friend, co-worker, relative) asking you to do something out of the ordinary, contact that person. It is likely that person’s e-mail account has been compromised.
Remember: an attacker can send out millions of e-mails with one click. If less than 1% of the people perform a foolish act, the attack is still very profitable. Don’t be part of the 1%.
Why Choose ASCERTIS Solutions
ASCERTIS Solutions can conduct a security assessment of a small business in a week and provide a roadmap for your company to implement a cyber defense strategy that fits your budget. Trained security professionals can be hired on a part-time basis to fill the role of Chief Cyber Security Officer (CISO) to assure that your roadmap is implemented in a timely and cost-effective fashion.
If interested, please contact assessments@ascertis.solutions.
